
Moscow’s online voting system has some major vulnerabilities, allowing votes to be decrypted before the official count
Мы говорим как есть не только про политику. Скачайте приложение.
Russia’s nationwide vote on constitutional amendments continued the country’s experiment with online voting, but only in the Moscow and Nizhny Novgorod regions. This time around, developers changed the voting system so that individual voters are guaranteed the ability to decrypt their own votes. On the one hand, this makes it easier to force people to vote. On the other hand, it could allow for a partial monitoring of the integrity of the vote count.
Moscow’s information technology department changed its voter encryption system
In 2019, Moscow’s information technology department developed a remote voting system using blockchain. As a result, votes were encrypted using the department’s own version of an ElGamal encryption system. Experts have found various vulnerabilities in this system on two different occasions.
Now, a voter’s ballot is encrypted with the help of TweetNaCI.js — a JavaScript library developed by a man named Dmitry Chestnykh. He found out that the developers of Russia’s remote electronic voting system were using his framework from Meduza.
Internet voters can now decrypt their votes before the official tally
Moscow’s previous encryption system encrypted each vote individually, using a unique secret key. Therefore, to decrypt your vote, you had to obtain the secret key from the recipient — in this case, the election committee.
The new system, on the other hand, issues a shared key to the sender and the recipient — in this case, the voter and the election committee — which can be used for encrypting the vote, as well as decrypting it.
In other words, a Moscow voter can now not only send their encrypted vote to the election commission’s server (where it will enter into the blockchain database), but also manage to decrypt it without having to wait for the election commission to start the official vote count and publish its secret keys. So long as the voter saves the secret key their browser generates when they cast their electronic ballot, they can decrypt their own vote.
To test the new system, Meduza ran this experiment on an electronic ballot that was cast using Google Chrome. As it turns out, getting your secret key is relatively easy: by saving the secret key, Meduza managed to decrypt the ballot of a voter taking part in the experiment (keep in mind that if you didn’t save your secret key, you won’t be able to decrypt your vote yourself until the election commission publishes it).
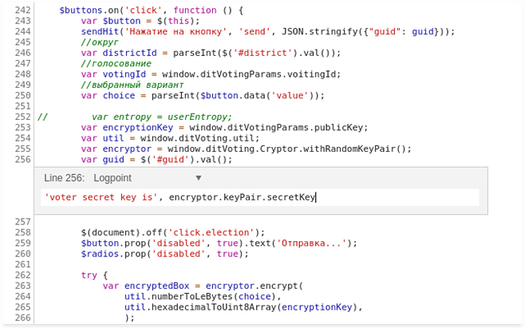
The bad news is this enables forced voting
Secret keys for encrypted votes being readily available to voters could put them at risk of coercion. In theory, now employers can not only verify that an employee actually voted, but also find out how they cast their vote (by demanding that they save their secret key). Furthermore, saving these encryption keys doesn’t require an employee to be technologically savvy. They could, for example, be asked to download a special browser extension, which replaces randomly generated keys with static ones. This would greatly simplify the task of decrypting votes, since they would all share a single encryption key.
The good news is you can monitor the vote count
That said, this same feature can be used for monitoring the integrity of the vote count, in the event that the election commission refuses to disclose the encryption keys for each specific electronic ballot (as was the case in 2019). For example, a particular candidate’s supporters could agree to install the same browser extension, which would allow them, over the course of the voting period, to track the minimum number of votes their candidate should be guaranteed during the final count.
The online voting system’s developers could ban voters from using a shared set of encryption keys, but this would be no use. Dmitry Chestnykh, the framework’s developer, suggested a number of ways for circumventing this kind of ban, including browser extensions that write seemingly random encryption keys that can be restored at a later date. “An extension could simply save the keys in a central database,” Chestnykh also suggested. “The Curve25519 algorithm is very fast, so decrypting millions of votes would be easy.”
“In any case, this is, of course, complete nonsense — not an electronic voting system,” Chestnykh said, in sum.
In order to close this loophole, Moscow’s information technology department will have to change its online voting encryption system completely once again. And it’s unlikely that this can be done before Russia’s unified voting day in September 2020.
Text by Denis Dmitriev, with special thanks to Mikhail Zelensky, Evgeniya Davydova and Dmitry Kartsev for participating in the experiment
Summary by Eilish Hart
(1) What’s that?
The ElGamal encryption system is an asymmetric key encryption algorithm system, proposed by Stanford University’s Dr. Taher Elgamal in 1985.